Configuring Apple MACs for use in an enterprise environment
We
currently own over 150 Apple computers, 20 which are MacBook Pro's and
the remaining amount being iMAC’s. All of our MACs are unmanaged and
require onsite assistance when issues occur.
These are some of the issues we experience when using MACs in our enterprise environment;
Our current setup;
What we have done to address the issues our users are experiencing;
The End
This is just my experience of using MACs within a corporate environment. I am not responsible for any damage caused to your network environment by following the content of this article - I am only trying to help someone out there.
I hope it helps you and gives you a pointer in the right direction. Comments welcome.
Thanks
References:
These are some of the issues we experience when using MACs in our enterprise environment;
- DNS resolution issues
- Proxy settings disappearing from the Network Settings for the Network Adapter.
- Constant bombardment of proxy authentication prompts once logged into the MAC for the first time using your Windows Credentials. There are two prompts for system HTTP & HTTPS and two prompts for the Safari Web Browser (HTTP & HTTPS).
- Safari Web Browser not set to the default home page for our company
- Printers have to be manually configured on the MACS
- Blocking of applications is too complicated for staff to manage (causes other issues with other programs)
- Attached network drives, home shares and memory sticks are not always visible on the users desktop
- All of the computers individually connect to Apple’s update repository wasting bandwidth
- Unable to perform any remote administration to the MACs
- MACs regularly showing ‘Network Accounts Unavailable’ (NAU) which prevents Active Directory users from logging into the MACs.
- Docks should be consistent with the most frequently used applications available to select instantly.
Our current setup;
- All Apple computers run 10.7.1
- All MACs joined to the Active Directory Domain
- NTP configured in clock preferences. This is important as if the time is out of sync with Active Directory then you may find the computer showing the error ‘Network Accounts Unavailable’
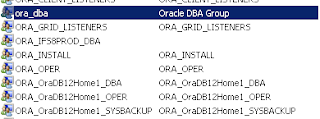
- Option specified to allow administration by network accounts via Active Directory Group Membership. See Reference 1.
- Modified the Search Policy to include a custom path. We found that adding the missing item within the authentication policy reduced the frequency which we would experience NAU error. All Domains is the last entry of the Search Policy.
- Users home directory available within the User Dock
- Windows printers manually attached to computer. See Reference 2.
- All computers are connected to the Microsoft ForeFront 2010 Firewall Web Proxy Service.
- Fully Functioning Windows Server 2003 Active Directory Domain
What we have done to address the issues our users are experiencing;
- DNS resolution issues - within the DHCP Scope, I have ticked the ‘Dynamically update DNS A and PTR records for DHCP clients that do not request updates.’ This fixes the issue of trying to contact the host name of the machine when trying to provide remote assistance.
- Computer Preferences - We have obtained an old iMAC, installed 10.7.4 MAC OSX and downloaded and installed MAC OSX Server. Once the MAC Server is installed, you can use the Work Group Manager (WGM) to create a Computer Account Group and configure deployment of settings such as;
- Proxy Configuration
- Browser Customization
- Login Messages
- Blocking of Applications
- Advanced configuration of Finder Preferences
- Printer Deployment
- Login Scripts
- Software Update Repository
- Dock Customization
Once the deployment is configured, you need to select computers who will be ‘members’ of that group. This is discussed next. See References 3 & 4 for help downloading and installing MAC Server
- Join the MACS to the Open Directory Domain and ensure the LDAP Directory for the MAC server is the last entry is the Search Policy. Once the MAC is joined to the OD (Open Directory), it is also necessary to bind it using an OD administrator account. Once this is complete, the computer will appear in the WGM. You need make sure the computer account is a member of a Computer Group within WGM. Once this is done, all you need to do is log out and back in and the preferences will have applied. If not, check;
- The MAC is binded to the OD domain properly
- You have an IP Address
- You have attached the MAC to the correct container which contains preferences
- Do some digging!
- Configuration of Software Update Server on MAC Server - Identify the URL and attach it to the preferences for the ‘Software Update Repository’ within the Computer Group Preferences. See Reference 5.
- All MACs updated to 10.7.4. The change log specifically states that issues have been resolved with ‘Improve the reliability of binding and logging into Active Directory accounts.’ We have instantly noticed the difference. An example would be some machines showing the NAU message. After the installation, the error message would disappear. See Reference 6 for list of updates.
- In order to provide remote assistance to the MACs, the following features within Sharing have been enabled;
- ‘Remote Login’ for Administrators only. This allows you to use SSH to connect to the terminal of the MAC and perform remote commands.
- ‘Remote Management’ for specific users (unable to select AD Accounts, but you can control another users account who is logged in if you have their username and password). If you click the Options button, you can select the ‘force VNC users to type in a password before connecting to this machine’.
- Installed TightVNC Client on our Windows Clients. Once the hostname is specified, we are prompted for the VNC password and then connected to the remote MAC.
- Multiple Proxy Prompts - This actually look a while to resolve. I was looking at third party software such as Centrify and Thursby which might allow me to use my current credentials to authenticate to proxy server but they all failed. The issue was related to the Kerberos ticket issued to the user from the Domain Controller once logged in. Although the Kerberos ticket was perfectly valid and allowed me to authenticate to other network shares without prompting me for a password, it would not allow me to authenticate against the firewall. The issue came down to the ServicePrincipleName (SPN) attribute attached to the computer account for the firewall. If a specified service is not listed, the Kerberos ticket is not allowed to be utilized. After I made the change to the SPN, all of the four proxy prompts disappeared after a reboot. If you specify the proxy server via IP address, you would have an SPN value of ‘HTTP/10.1.1.1’ for example. See Reference 7 for my support query within Microsoft’s Forums and Reference 8 which helped me resolve the issue from McAfee.
- Login Scripts - we have used a simple bash script which runs as root to apply various settings such as disablement of the 'Cloud' popup storage notification.
The End
This is just my experience of using MACs within a corporate environment. I am not responsible for any damage caused to your network environment by following the content of this article - I am only trying to help someone out there.
I hope it helps you and gives you a pointer in the right direction. Comments welcome.
Thanks
References:
- http://support.apple.com/kb/HT4332 - Adding Network Groups to Adminster MAC
- http://support.apple.com/kb/HT3049 - Adding SMB Printers
- http://www.apple.com/osx/server/how-to-upgrade/ - How to download MAC OSX Server
- http://www.dummies.com/how-to/content/how-to-create-an-open-directory-master-using-lions.html - How to install MAC OSX Server
- http://support.apple.com/kb/HT4069 - Software Update Service
- http://support.apple.com/kb/HT5167 - MAC 10.7.4 updates
- http://social.technet.microsoft.com/Forums/en-GB/Forefrontedgegeneral/thread/3c6a6c16-0ac0-41c4-95ab-cfaf19c04f31 - Kerberos Authenication
- https://community.mcafee.com/docs/DOC-2682 - Configuring Kerberos for Web Gateway on McAfee
Comments
Post a Comment